Liher Elgezabal: "Cryptography is art and science on the one hand"
Hi Liher, you are working in London. How?
The main reason for coming to London was curiosity. I am very fond of Linux and free software and, as at that time the use of this type of software was quite limited, I decided to come abroad. Since then I have been working in London and New York and have had the opportunity to study.
What do you do at Micromuse? And what exactly do you do?

Micromus develops software. We perform applications to monitor the security of data networks in real time and are used by large telecommunications companies to control giant networks.
I work in the software quality control department, looking for programming errors and security of our programs. I am developing a bug finder that does it automatically.
In the subject of cryptography, that sense of security in computer communications is false, right? Is it easy to detect messages circulating on the network?
Unfortunately, today security is entirely in the hands of users, as the internet does not offer any security.
In ordinary mail, if the message is sent without envelope, the mail will be able to read the messages. The same goes for email.
Network deployment has greatly facilitated communication but we have no control of the network, that is, the communication channel.
Is it common to detect messages? What are the main reasons?
Since writing exists, man has tried to detect written messages. The reasons can be very different, from mere curiosity to economic, political or military reasons. Information has always been a highly valued resource.
Most current communications are transmitted and stored digitally, greatly facilitating the capture, copying, filtering and other automated data processes.
Our personal information, clinical history, banking movements, phone call lists, etc., are stored digitally and this information is generally dispersed over the network. This affects the need to adequately protect information.
It can be thought that, being a normal user, no one will be able to detect your messages or if it detects them it does not matter.
Although the value of our information is small, it is very rare to send a letter without envelope. We would feel observed because we are aware that the letter has to go through various means. A person generates more distrust than a machine, but we must remember that behind all machines there are people.
Privacy is a legally protected right in most countries. However, the institutions that create them are the ones that most threaten this right. If the law does not protect us, we have to protect ourselves from mathematics.
What if you want your messages to be read by a specific recipient, and not by another, is cryptography necessary?
In principle yes, as long as the channel is not safe, we will have to somehow protect the message, and for this the way is to use cryptography. In fact, it is something that has always been done.
Julius Caesar kept his messages with a certain code to make them incomprehensible to his enemies. At the same time, the writer of La Celestina concealed his identity between the lines of the book to defend himself.
Today, thanks to the capacity of computers, complex mathematical functions are used to encrypt and hide messages.
What is cryptography? What is it?
Cryptography is art on the one hand and science on the other. The goal is to make incomprehensible texts, sounds, images or any other type of information.
Cryptography is based on making transformations on the original text, modifying the position of the letters (displacement) or substituting (substitution). For example:
elhuyar --- (swapping for couples) --- leuhayr
elhuyar -- (alphabetically + 3) --- hñkybdu
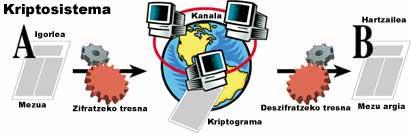
A cryptography algorithm defines how these transformations are carried out. The algorithms currently used are public and known. These algorithms will transform information in one way or another depending on a variable. This variable is called a key. Cryptosystem security is key, not in the algorithm itself.
Is there a single message encryption system? What is the difference between systems?
As we mentioned, we need a key to encrypt our messages and keep the key secret. According to this key two different cryptography systems are distinguished.
Symmetric cryptography uses the same key to encrypt and decrypt the message.
Imagine that we have a safe box in which we want to keep our secrets. The lock is closed by a 3-digit combination. If we have used the 0-7-4 combination to close it, we will have to use the same extended combination.
Asymmetric cryptography, however, uses additional keys to encrypt and decrypt messages. A key can only decipher what numbers another and vice versa.
Suppose when designing the safe we have fixed that the sum of the two keys should be 8-0-0 and that this data is only known to us. If we have used the 2-0-0 combination to close the safe, we will have to use the 6-0-0 combination to expand.
Using this system, the encryption key (in this case 2-0-0) can be made public as it is not used to decrypt. The message can be encrypted by anyone, but only we can decrypt it. Knowing one key is not possible to calculate the other, since the sum of both (8-0-0) is unknown.
Encryption programs will also be several. Do all serve the same?
The best known example is the free program PGP (Pretty Good Privacy). It was designed for the use of secure email, although it supports other uses. Thanks to the PGP it has been possible to bring the solid cryptography that until then was in the hands of governments or military institutions to regular users.
Another implementation that we are increasingly using is the so-called X.509. The best-known browsers incorporate this standard and are used to steer e-commerce securely.
The only purpose of cryptography is to protect messages?
No, at all. Hiding the message is a possible use, but cryptography has other applications. It allows, among other things, to ensure the integrity of the message or to verify the identity of the author of the message. These last two are the basis of the digital signature.
Of course, there will be systems for capturing and reading unauthorized messages.
Cryptoanalysis analyzes the unauthorized reading paths of a cryptogram.

Each language follows several repetitions of letters. You can also analyze the number of times some letters appear in each language. Given this information, it could be assumed that the letter Y that appears an X% in the cryptogram may be originally.
Is the cryptosystem completely safe to finish?
Cryptography protects a great secret (our message) from a small secret (the key). And the robustness of current cryptographic systems is based on the length of the key.
As with the safe, when using 3 digits there are only 1,000 different keys, so the alleged aggressor will not take long to make several opening attempts.
As it is possible to test all possible keys, there is no true secure cryptosystem. But if the time or cost required to decrypt a cryptogram is greater than the value of the information, we can say that it is a robust system.
A computer, even with a million attempts per second, will need more than a thousand years to demonstrate all possible 56 bit keys. It is clear that by then the information will lose its value.
Isn't it uncomfortable to walk with keys and cryptographs? Does it require a lot of work for the user?
Message encryption and decryption is immediate with the PGP program. However, before we start encrypting messages, we must install the program, create the key pair (public and private) and distribute the public key. This work is not particularly complicated. However, in my opinion, the most difficult thing is to explain to others what cryptography is and why they should use it.
And in your case, you're thinking about staying in London. Is it not possible to act in the area where you work in Euskal Herria?
The truth is that today in the computer world the word distance has also lost meaning. Although I am in London, I work on computers in New York through the network.
The incorporation of the new technology in the Basque Country is being very fast and the need for qualified technicians is increasingly evident. I also intend to go home someday, but for now I am satisfied here and I have many left to study and see.
Buletina
Bidali zure helbide elektronikoa eta jaso asteroko buletina zure sarrera-ontzian








