A hole in the perfect wall
2010/07/01 Elhuyar Zientzia Iturria: Elhuyar aldizkaria

First quantum cryptography hacking
Some Toronto researchers claim to have developed a method to overcome the safest cryptography available (hacked): quantum cryptography. This message encoding method is already on sale and is used by some banks. In fact, researchers in Toronto have hacked the ID-500 system, a commercial system for transporting the key to quantum encryption developed by the Swiss company Quantique.
Much has been written to say that quantum encryption is a perfect coding system, and that idea is widespread, but it is not true. Experts have insisted on numerous occasions that all encryption systems have a weak point, although it is true that quantum encryption is much safer than any other method, by far, so apparently you cannot decode the encoded quantum.
But it is possible and Canadian researchers claim they have achieved it. Quantique refuses and a theoretical debate arises.
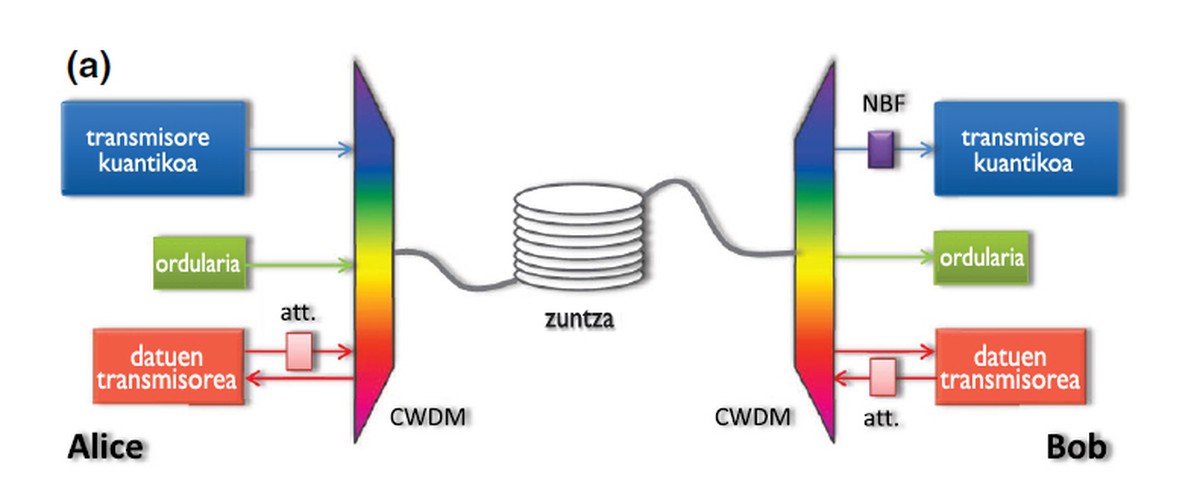
Quantum encryption is based on a simple principle: that it is not possible to know the quantum state of a particle without modifying the same particle. These particles are photons in the banking key transport system, small pulses of light from a laser sent from the optical fiber. And normally the polarity of this light is used to encode messages. Therefore, whoever wants to decode the message should know what the polarity of the light is.
However, at the quantum level, this information can only be consulted once, by the above-mentioned principle, since the photon changes in this process. Taking advantage of this, quantum encryption performs two transmissions for each message, one is the same message and the other is the key to decode the message. If the message receiver detects changes in the photons --there are several systems to do so -, the key transmission is not performed and the message transmission is considered incorrect. That is why quantum encryption is so good, as when any interference occurs it is physically detected before transmitting the key.
Theory has been a great hope. The system has, however, a weakness, a practical technological problem: there is no optical fiber that can transport those small pulses of light perfectly. There is always a small loss, always changes a small batch of photons, so the one who receives the message would always give bad transmission (he does not know why photons have arrived changing, if it is an interference or if it is consequence of the transport of the optical fiber). Therefore, no rigorous action is taken and a degree of error is allowed, usually up to 20%. Up to this limit, changes in photons are considered background sounds of the signal.
Toronto researchers have made a pre-publication in the electronic journal arXiv, in which they claim that to decode the messages the background sound takes up a maximum percentage of 19.7%. However, Quantique's claim that their system does not support such large errors, that their system breaks transmissions above 8%.
If the latter is true, the ID-500 system is safer compared to systems that use conventional error, as it only supports 8% error and not 20% conventional. But, in return, they will have much greater technical problems in the transmissions, and they will have to give for good much less transmissions. According to Toronto researchers, the ID-500 encryption system has been hacked and, according to Quantique, they have not succeeded. But the debate is not just theoretical: the customer who buys the system will have the last word.

Gai honi buruzko eduki gehiago
Elhuyarrek garatutako teknologia