Pintxo-pote kontuak, blockchain to eta bitcoin a
2018/09/17 Ander Galisteo Zabalo - IMDEA Networks Institutua (Madril); Carlos III Unibertsitatea (Madril) Iturria: Elhuyar aldizkaria
The benefits of the Internet are undeniable. For the first time we have a tool that connects the whole society. However, this connection has created a new paradigm. Users cannot know if the person across the network is reliable. So how can we get everyone to share information without anyone replacing anyone's identity and changing private information?
This article will analyze the best-known solution that has been found in recent years to solve this problem, taking as an example the realization of accounts with friends such as blockchain or blockchain[3][6]. For this, in the first place, a series of essential concepts will be presented to understand what blockchains are, as well as the benefits and problems that can entail.
What are blockchains?
Imagine that we are with friends, for example, in the pintxos boat of the San Sebastian neighborhood of Gros. How do we pay for our pintxos boats? On the one hand, it is possible that everyone pays their own, but it is clear that it is not the most efficient option, since it would cost us a lot of time to pay. Another option would be to put a pot among all, because we would pay much faster. However, this poses other problems: What if the tin money wasn't enough? What if it's over at the end? Many times not all prices are the same, in this case, how would we distribute the price?
In view of these problems we can think of a more suitable solution. We will create an account in which each member puts in each bar how much he owes and who he owes. To make this account as transparent as possible, instead of being written on paper, all data will be online so that everyone can see them, for example, in a WhatsApp group. But what if team members were not reliable? Let's see what tricks we can use to solve this reliability problem. After all, the blockchain is just that, a huge account that every participant can use to write transactions between them. Let us therefore see what a transaction is.
Transaction
As already indicated, it will appear in the account how much and to whom each person owes in each bar. There are two ways to do this: who pays notes it in the account or who owes it writes it. It is clear that the first option is not convenient, since if any participant missed money you could consider that others owe you. Therefore, it will be the debtor who notes the amount and to whom it owes. Thus, we will ensure that no one will cheat because writing something in the account will lose money. This is called a transaction in block strings. But how can we know if he is really able to pay the amount he has written? Very easy. Each time a transaction is written, each person who is in that account (in this case in the WhatsApp group) must check whether the debtor has enough currency to pay the transaction. If not, the transaction is cancelled. And how can we know if he has enough? Simply because looking at all the previous transactions we can know if you have enough to settle the debt. At this point we can already detect where the value of the account is (in our case the WhatsApp group): we can use in a new jar of pintxos the amount that I have previously owed. However, how can we ensure that I only write my transactions?
Digital signature
Digital signature[1] arises to solve a single problem: verify the origin of a message. Although humans see a message as a set of letters, a computer sees a message as a set of bits (any file, to be sure).
Suppose we have many users. The digital signature creation algorithms are two: the first is used to create the signature and the second to verify the signature. Each user has two codes called key, one private (Iphone) and another public (Gpu). The signature creation function is:
signature = signature (iphone message)
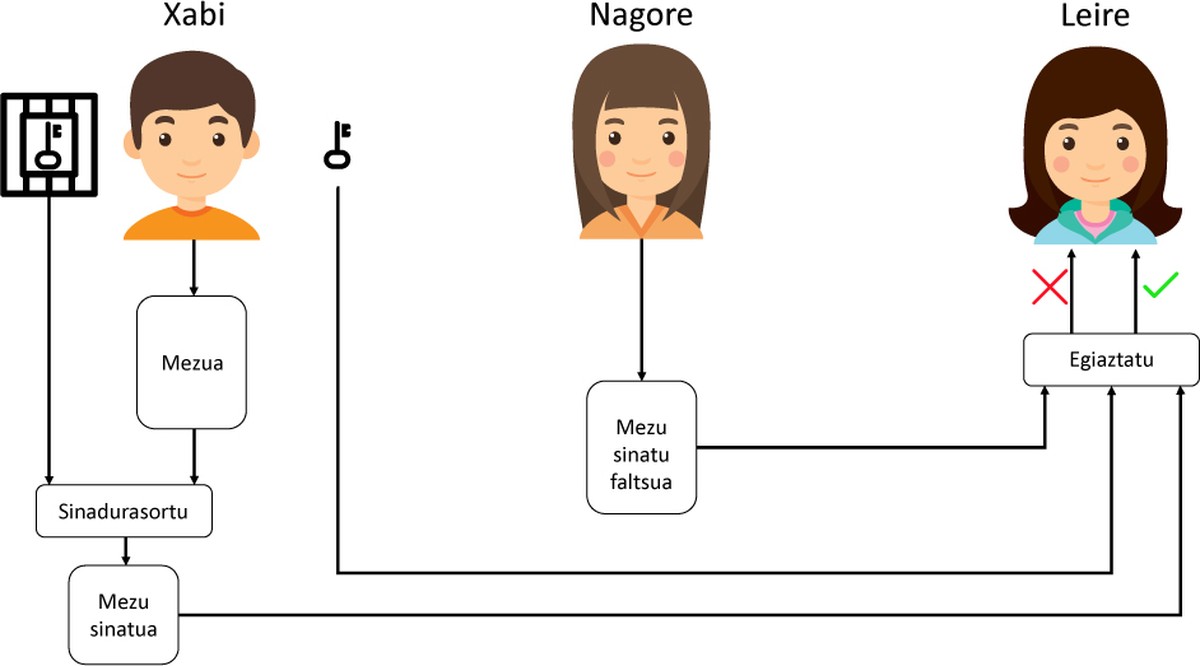
Here we perceive the most significant difference between people's signature and digital signature. As you can see, each signature is created for each message and user, so the digital signature will depend on the message and the user (people use the same signature to sign all documents). This means, among other things, that we can use our GPRS in different messages without losing security.
On the other hand, we have another signature verification function:
if/no = check(message, gpu, signature)
This function tells us the origin of the signature using the signature, the message and the public key. In this simple way we can know if the message has been sent by the user that we really want. For example, see figure 1.
Block
What we have said so far would be useful in a small gang, and could be applied smoothly. But normally in the poteo of pintxos we do not usually be with the crew, normally we find those of the sports team, of the university, of the members of the dance group... and in this case we do not serve what we have done with the gang. So let's do the WhatsApp group in San Sebastian, a group that includes all Donostians. And is there someone from Vitoria? Let us then make the Euskadi team. And is there anyone else? Well, let's make a world team. But now we have a big problem. In a WhatsApp group worldwide, it is clear that we will not be able to read all the messages and it will still be more difficult to check all the transactions (messages): we will not know who you owe, nor in what order the transactions have been made (it is not the same to spend after receiving the money that spend the money first and then receive the money, which is not legal). Therefore, in a large account it is essential to join transactions in a fixed amount by creating blocks[5]. Therefore, each WhatsApp message will be a set of transactions.
However, we may think that this does not solve the problem, since now instead of a lot of transactions we have a lot of blocks. If each user creates a block we will not solve the problem. Therefore, it should be difficult to create a block for a user, but simple for other users to know if the block is well created. How can we do it?
Hash functions
Hash[4] functions are very useful functions for converting a dataset into known size data.
hash = hashfunction (message)
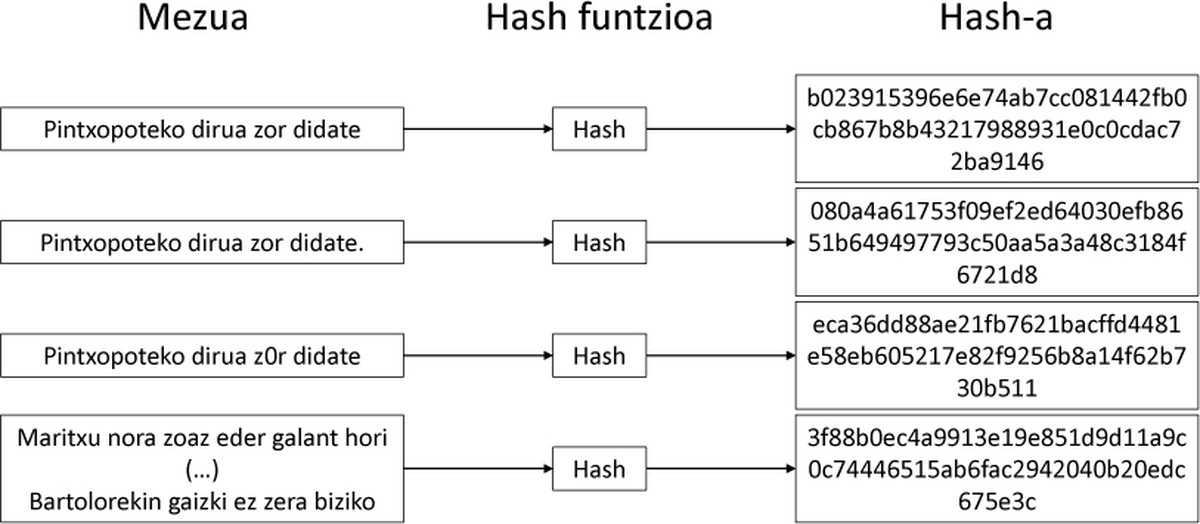
However, Hash functions have a very special property: if we change the message a bit, the output will vary a lot. The change is so great that we find it random to output two very similar messages. Figure 2 shows a clear example.
Therefore, if you give us a message, it is very easy to get your hash, but with the hash we will not be able to know what the original message was. The only way to get it is through rehearsals, changing the message until you get the desired hash.
And how can it help us? A block (a set of transactions) is just a message. Thus, we can find the block hash, always keeping in mind that the hash of our block will vary depending on the content and order of the transactions.
Now let's write something at the end of the block, a character set. But why?
Proof-of-work
A restriction is going to be placed on blocks: the block hash has to have several 0 at first. To achieve this, as indicated above, at the end of the block we will write a set of characters called magic number. As we said, it is not possible to return from hash to message, since the only way to get 0 is to try many combinations of characters until you get the desired amount 0. This calculation consumes many computer resources (time and electricity). This means that if a block has a hash of many 0, someone has spent a lot of energy on calculating it, making it a reliable block.
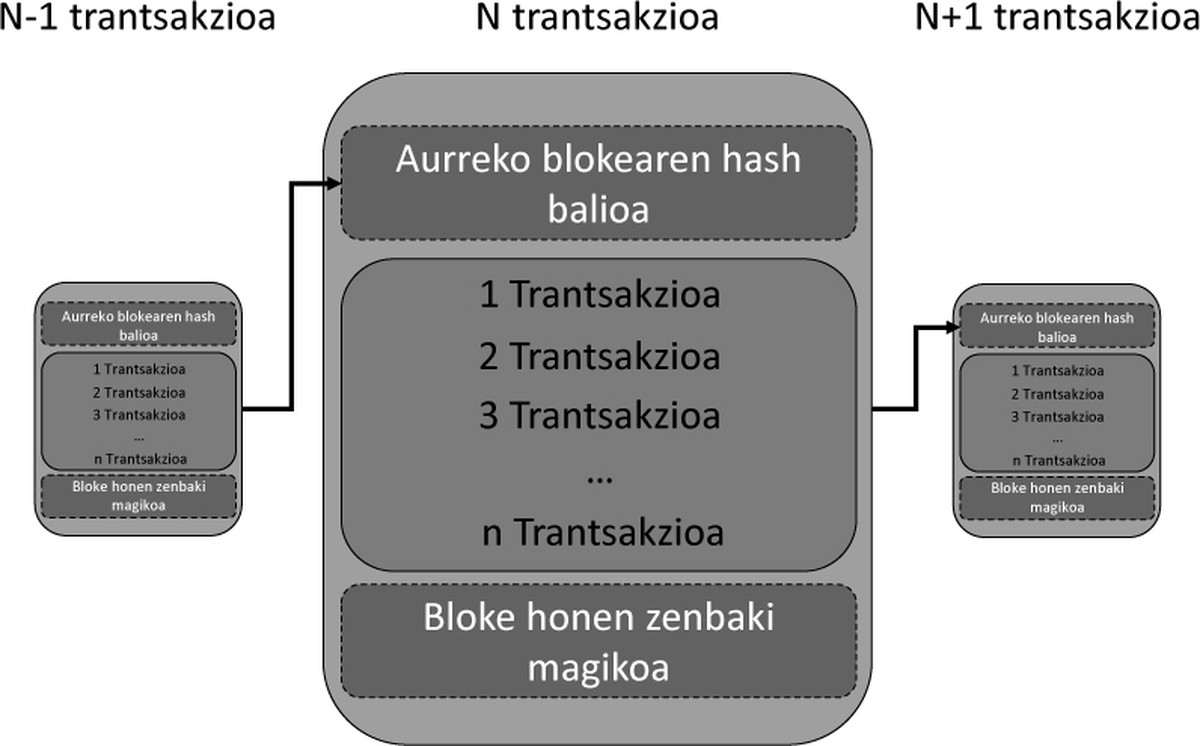
As we said, it is easy to check if the hash rule is met. Therefore, it makes no sense to try cheating, as they would catch them easily. But why would people do it? Why do all these calculations to calculate the block hash? The answer is simple, because there is a prize for whoever first creates the block. This prize is only a value within the account: in the example of the gang the food or drink for the poteo of pintxos, in the case of the vitcoina the bitcoinas. This process is called mining. The block is completed with the previous block hash. Thus the blocks are ordered. Figure 3 shows the structure of the block.
Relationship between block chains and bitcoine
But then how do we relate the structure we have described (blockchains) to the most famous cryptomonet in the world? Blockchain is just a concept, a way to keep accounts. Currency of Bitcoina blockchain, electronic currency to carry accounts using blockchain. In the same way, the sum is only a mathematical concept and an expression of "5+2".
Conclusions
Although more unknown, this article has attributed greater emphasis to blockchain than vitcoin. Why? Because in addition to vitcoine there are many other cryptomonets (ethereum, litecoin, dash..), but they are all expressions of the same concept: blockchains. Cryptomonets can rise or fall on the market, can be created and disappear. In any case, it is clear that blockchains will be present in our life in the coming years in cryptomonets to share information or, perhaps, to avoid pintxo-poteo problems.
References
[1] Whitfield Diffie and Martin Hellman. New directions in cryptography. In: IEEE transactions on Information Theory 22.6 (1976), pp. 644–654.
[2] FileFormat.info: Hash functions. for example. fileformat . info / tool / hash.htm
[3] Satoshi Nakamoto. Bitcoin: A Peer-to-Peer Electronic Cash System. November 2008. 2015
[4] Bart Preneel. “The first 30 years of cryptographic hash functions and the NIST SHA-3 competition”. In: Cryptographers’ track at the RSA conference. Springer. 2010, pp. 1–14.
[5] Melanie Swan. Blockchain: Blueprint for a new economy. O’Reilly Media, Inc., 2015
[6] Youtube channel 3Blue1Brown: Ever wonder how Bitcoin (and other cryptocurrencies) actually work? https://www.youtube.com/watch? v=bbc-nXj3Ng4.

Gai honi buruzko eduki gehiago
Elhuyarrek garatutako teknologia






