Malware, the nightmare of systems

What has been considered the first portrait was created by Robert Thomas Morris in 1972. It was known as Creeper on the computer monitor "I'm a creeper... catch me if you can!" (I am Aihen-belarra, hurry me if you can!) because from time to time he showed the message. Of course, the first virus brought the first antivirus program: Reper, in Basque, mower. However, the word virus did not appear until 1984.
What are viruses?
A virus is a small program that reproduces automatically and reproduces without knowledge and authorization of users, introducing part of its source code into the source code of other applications. This way, when the contaminated application is executed, the source code introduced by the virus is also executed, which is integrated into other applications or files. And when these infected files run on other systems, this system is also contaminated and the virus source code is copied into the files of the new system. This is the main goal of the virus: to spread itself.
However, they have been popularized by the damage they cause in the multi-virus system. This is what is known as the payload of the virus, that is, the consequences of viruses in the system. The consequences can be simple jokes or major damage to data or the network, for example. However, and as believed, a computer virus is powerful for its reproductive capacity and not for the severity of the damage it can cause in the system.
Viruses, in general, should know if a file is infected to prevent it from spreading again, leaving a signature or a mark on infected files. For that is the vulnerability of viruses to survive. In fact, once the brand is known, antivirus can detect virus and infected files.
The more accurate the brand is, the easier it is to know and detect it. Therefore, virus programmers try to develop the most generic marks possible and not use certain characters as trademarks, but they can also contain uncontaminated files. This will prevent all system files from being infected by the virus, but at the same time will make it difficult to capture. There have also been unsigned viruses, such as Jerusalem. It infects files repeatedly and collapses hard drives.
Viruses are not the only risk
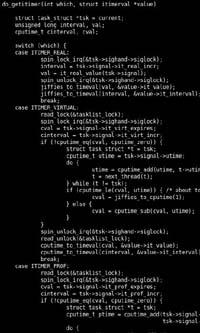
As mentioned above, all harmful programs that can be introduced into computers are not viruses and currently systems are threatened by various malware. Among them, the Trojans enjoy a certain prestige. Unlike viruses, they do not have automatic reproduction capacity. In fact, its historical name indicates that it is a harmful application, but it is introduced into the system as a harmless application. That is, in a normal application that can be used normally a harmful source code is introduced that attacks: it is a useful application for the user, but below it is executing other functions without the user realizing it.
The first Trojan appeared in 1980, but before the Internet was spread it was not much used, since it had to be distributed manually. Now, however, they are easier to distribute and are quite dangerous because they are destroyed slower than viruses. This is the main objective of the Trojans: to persevere unconsciously in the system in order to perform their tasks. These tasks can consist of erasing or replacing data, receiving user information, monitoring the user screen, giving access to the computer, etc.
One of the tasks of the Trojans is to introduce spyware or spy applications. Spyware run by themselves on the system and its main goal is to obtain information from the system and user: data, operations, visited websites, read information, etc. And as the information of these applications is sent over the Internet, the collateral effect of spyware is to reduce the speed of Internet connection.
Like spyware, backdoor or back doors can also access systems via Trojans. The Trojans can have the rear door open, so that the backdoor can be a file that the user has downloaded and installed from the Internet, without being aware of it. These backups are nothing more than fragments of source codes that allow access to polluting systems and allow the aggressor to avoid direct access authentication pathways to the system. Once inside, the contaminated computer can monitor user operations, print, open DVD or CD-ROM readers, access or save files, etc.
Another known malware is worms. Like viruses, they are automatically reproduced, but unlike viruses, to reproduce they should not contaminate other files, but they start automatically with the system. In this way they manage to locate the user in the memory, between the processes of the system, without realizing it. Its objective is to spread through the Internet or the local network and access other computers. Logically, the workload of the reproduction process of males makes the system and the Internet connection slow down.
One of the best known has been Blaster. A security failure of MS Windows systems at the time led to a rapid expansion in the local network or over the Internet, restarting the system in a minute.
When clicking means a loss of money

The frauds that occur on the Internet have become an important danger in recent times and is a worrying problem, since its fall can be a loss of important money. Perhaps the ear is Phishing (arrantzan, euskaraz). Unlike the malware mentioned above, they are not installed on systems or automatically reproduced. They are located on an Internet server and must access their website through the browser.
The most common way to access this address is through an email that, supposedly, has been written by a financial entity or by a known company and requests the reader to access its website through a link. Both the domain and the design of this website are as similar as possible to that of the real entity's website to deceive the user. And, with any excuse, it requests the user some of his data that, in general, are necessary to operate on the Internet with the financial institution. In this way, the aggressor can obtain the data of the user to be able to operate in his account.
Another malware that incites over the Internet is the dialer, but it is not so widespread. And they have to make a call to put the manure through the modem and no call is made through ADSL or cable modem and routers. The dialers are, in fact, small programs that hang on the web pages. They ask the user to download and run the program to be able to access some service. But something else happens: these small programs make remote calls without the user knowing it. As a result, the user receives a huge bill from the phone and the aggressor can get an economic benefit. To protect themselves legally, they usually mention it in a note of both the program and the web, of course in the small letter.
Vulnerabilities of systems
Faced with malware, the main weakness is not in the system, but in the behavior of the user, since most of these malwares are used for what is known as social engineering to infect the systems or put manure. That is, by means of manipulation techniques and subgames the user gets to run an application or click on a link.
However, in systems there are features that make them more vulnerable to malware attacks. For example, the so-called overflow buffer overflow or buffer overflow is a weakness widely used by malware. This error occurs when the structure designed to store data in a memory space allows to store more data than included in its capacity. Some malwares take advantage of it to run the source code.
Another of the weaknesses is that if you use the same operating system on all computers on a network, if you get access to it you will also be able to access all computers on the network.

Likewise, the granting of permissions to programs and users of the system above those strictly necessary can be counterproductive. System management permits are often granted to the user who is not a system administrator, by default in the configuration of some systems.
Measures of protection
Many of the measures that can be taken to protect the system can be derived from the above. The main thing is that no applications are executed that are not well known and that no data is given without certifying who is being provided, and of course, no more data is given than necessary. It must be taken into account that financial institutions never request by e-mail access data to their websites.
In addition, other simple security measures can be adopted, such as, for example, with the permissions required by which we are only working, or log in with users with more permissions only when you need to install an application or change some system configuration. When a file is received via the Internet or another way, the absence of a virus will be ensured and the relevant data will be backed up. Likewise, it is important to keep the operating system updated.

Buletina
Bidali zure helbide elektronikoa eta jaso asteroko buletina zure sarrera-ontzian











